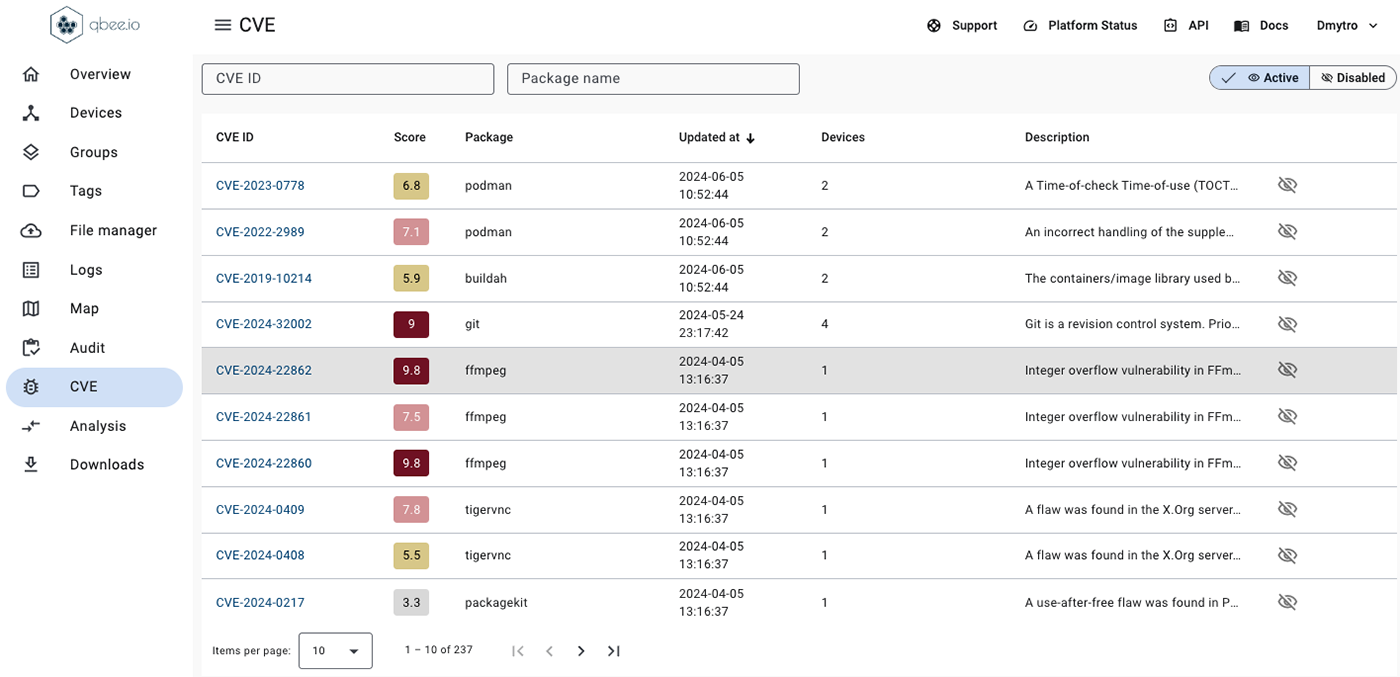
CVE
The CVE menu allows to see all detected CVEs as well as receiving additional information about the CVE details. Statistics are available about which devices are impacted by any specific CVE.
The list of CVEs can be checked and non-relevant CVEs can be disabled.