Users
When you create a new account on qbee.io, the first user is automatically given a default role. This role has full access to all areas of the platform. You have the ability to create new roles and assign these to any user. If a user is assigned multiple roles, they will have a combination of all the permissions from each of their roles. This means they can access and use everything allowed by each of their roles.
Using one mail address for multiple accounts
qbee identifies the accounts by the user mail address. This means that you cannot use the same mail address for multiple accounts. If you need to create users in multiple accounts we recommend to extend your mail address with a "+org". So user@example.com can create a new user having the following address: user+org2@example.com. All mails and communication will be received in the original user mailbox while the user name is uniquely associated with the second account.
Users management¶
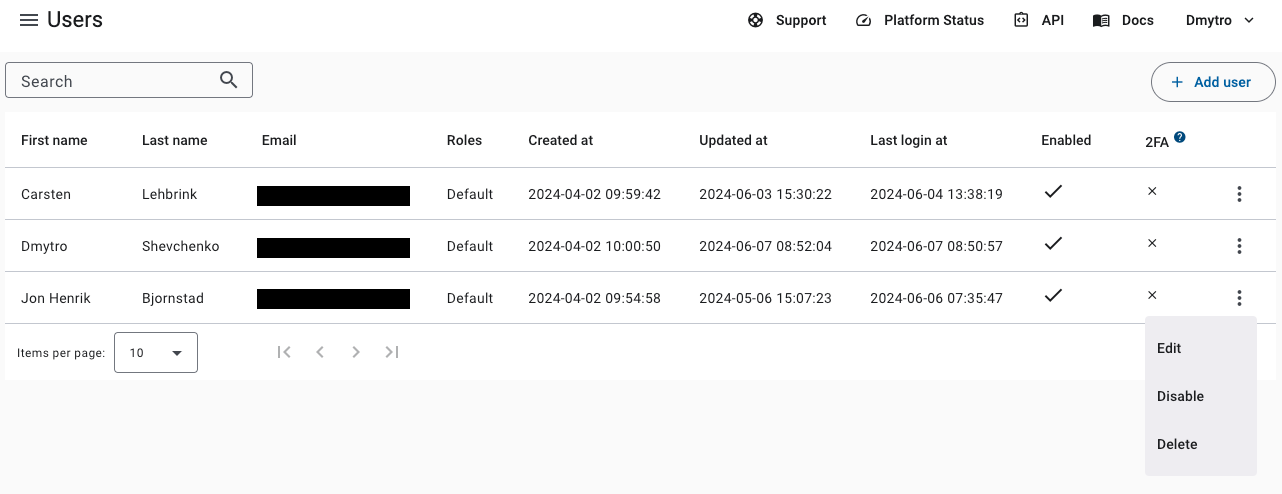
To see a list of all users, go to the Users section (top-right menu). From here you can see and search all users in your company, add new users, edit, disable and delete existing users.
Creating a new user¶
- In Users section, click on the
+ Add userbutton. - Enter the first and last name, and email address of the new user.
- Select the role(s) for the new user.
- Click on the
Createbutton.
Once the user is created, they will receive an email with a link to set their password. New users need to accept Service Agreement before they can log in.
Editing a user¶
- In Users section, find the user you want to edit.
- Open the actions context menu (
⋮) and selectEdit. - Change user details and/or roles.
- Click on the
Savebutton.
Disabling a user¶
- In Users section, find the user you want to disable.
- Open the actions context menu (
⋮) and selectDisable.
Disabled users cannot log in anymore and are not counted towards the number of users in your subscription.
Deleting a user¶
- In Users section, find the user you want to delete.
- Open the actions context menu (
⋮) and selectDelete. - Confirm the deletion.
Deleting a user
Deleting a user has immediate effect and cannot be undone.
Profile management¶
In the Profile section (top-right menu) you can change your personal details and password.
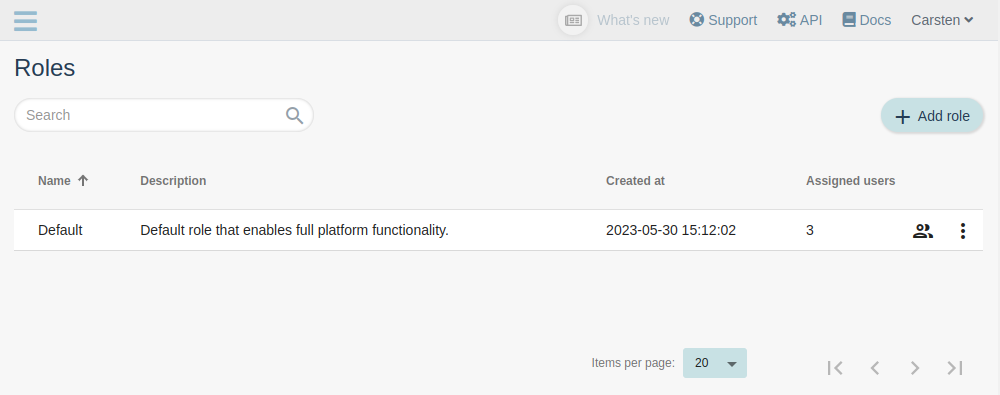
Roles management¶
To see a list of all roles, go to the Roles section (top-right menu). From here you can see and search all roles in your company, add new roles, edit and delete existing roles.
Creating a new role¶
- In Roles section, click on the
+ Add rolebutton. - Enter the name and optional description of the new role.
- Select the permissions for the new role.
- Click on the
Createbutton.
Editing a role¶
- In Roles section, find the role you want to edit.
- Open the actions context menu (
⋮) and selectEdit. - Change role details and/or permissions.
- Click on the
Savebutton.
Deleting a role¶
- In Roles section, find the role you want to delete.
- Open the actions context menu (
⋮) and selectDelete. - Confirm the deletion.
Deleting a role assigned to users
You cannot delete a role that is assigned to one or more users. You need to reassign the users to a different role first.
Resource-based access¶
Qbee.io allows fine-grained access control to managed devices through the use of string-based filters in the form of tag:<tag-name> and node:<node-id>. These can be applied to a subset of the available permissions for a role. The currently supported permissions are:
- device:read
- device:manage
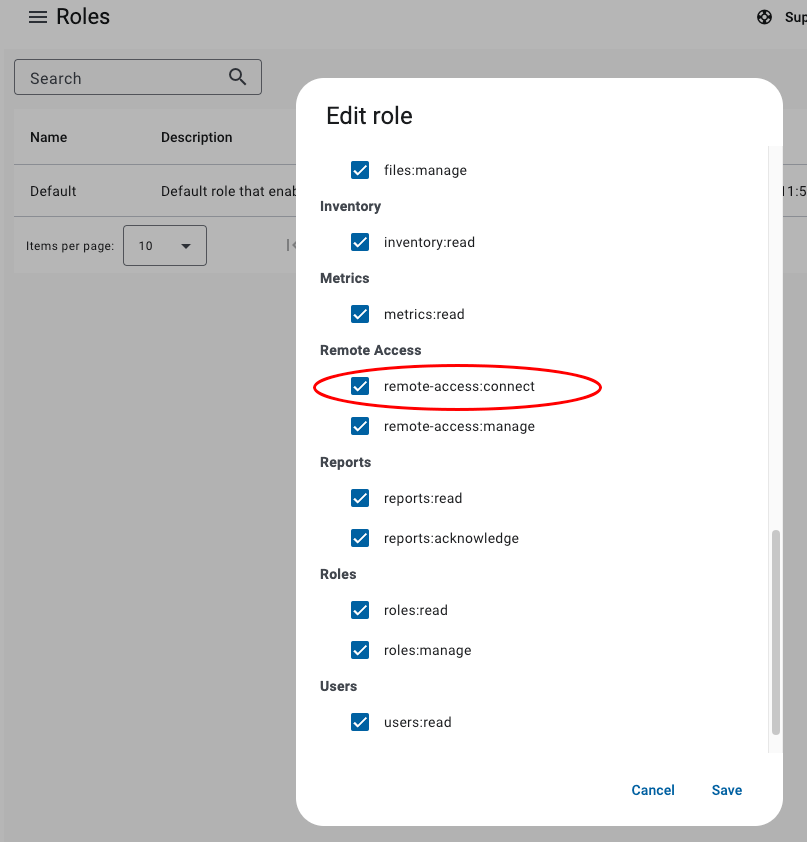
- remote-access:connect
- remote-access:manage
- reports:read
- reports:markread
Each of these permissions can be configured for a set of tags and node ids that are OR'ed together. Eg. if want a role to have access to devices with tag my-device-tag or devices that belong in a group with node id f6fb0cb4-496f-4c40-8a23-fa2f8d9a9074, the resource description for the permission should be defined as tag:my-device-tag and node: f6fb0cb4-496f-4c40-8a23-fa2f8d9a9074. Node ids for groups can be found by clicking the icon next to the group name on the group overview page. If no resources are defined, it is assumed that the resource description is the wildcard * which mean all devices.
Separation of responsibilities
Resource-based access typically comes in handy when you want to define some operational separation of responsibilities. It allows defining which parts of the fleet a user should have access to, eg. for first-line support or troubleshooting during a development phase.
Permissions¶
Each role consists of a set of permissions. The following permissions are available:
| Permission | Allowed API calls |
|---|---|
| analysis:read | GET /analysis POST /analysis GET /analysis/orgstats |
| audit:read | GET /commitlist |
| billing:read | GET /stripe/subscriptions |
| billing:manage | POST /stripe/create-customer-portal POST /stripe/create-checkout-session DELETE /stripe/cancel-subscription/{uuid} |
| bootstrap-keys:read | GET /bootstrapkey/{bootstrapkey_id} GET /bootstrapkeylist |
| bootstrap-keys:manage | PUT /bootstrapkey/{bootstrap_key} POST /bootstrapkey DELETE /bootstrapkey/{bootstrap_key} |
| company:read | GET /company/{company_id} |
| company:manage | PUT /company/{company_id} PATCH /company/{company_id} |
| configuration:read | GET /change/{sha} GET /changelist GET /commit/{sha} GET /config/{type}/{item_id} GET /configpreview/{type}/{item_id} GET /config/{device_id} GET /configpreview/{node_id} |
| configuration:manage | DELETE /changes DELETE /change/{sha} POST /change POST /commit |
| cve:read | GET /cve/{cve_id} GET /cvelist GET /cvescorestats GET /cve_hosts_max_count |
| cve:manage | PATCH /cve/{cve_id} GET /cve/status/cves DELETE /cve/{cve_id} |
| device:read | GET /grouptree GET /grouptree/{node_id} GET /node/{node_id} GET /groupreportssummary/{group_id} GET /deviceattribute/{device_id} GET /tagslist |
| device:manage | PUT /grouptree PATCH /deviceattribute/{device_id} DELETE /inventory/{device_id} PATCH /grouptree/{node_id} |
| device:approve | POST /pendinghost GET /pendinghost DELETE /removeapprovedhost/{node_id} DELETE /pendinghost/{node_id} |
| files:read | GET /file GET /files GET /file/stats |
| files:manage | POST /file POST /file/createdir PATCH /file DELETE /file |
| inventory:read | GET /inventory/{device_id} GET /inventorylist GET /inventory gGET /inventoryreport/{device_id} GET /inventoryreport/docker/{device_id} GET /inventorysummarybytype/{node_id} GET /inventoryonlinestats |
| remote-access:manage | POST /qbee-connect/portmap PATCH /qbee-connect/portmap |
| reports:acknowledge | PATCH /reportmarkread |
| reports:read | GET /reportlist GET /reportsummary/{device_id} |
| roles:read | GET /role/{role_id} GET /roleslist GET /permissionslist |
| roles:manage | POST /role PUT /role/{role_id} DELETE /role/{role_id} |
| users:read | GET /user/{user_id} GET /userlist |
| users:manage | POST /user PUT /user/{user_id} PATCH /user/{user_id} DELETE /user/{user_id} |
Permissions used in the UI
Certain parts of the UI are only visible when the user has the corresponding permissions assigned through a role. Following is the list of UI elements and their corresponding permissions:
| UI Element | Permission |
|---|---|
| Dashboard | analysis:read device:read inventory:read metrics:read reports:read |
| Devices | cve:read device:read inventory:read reports:read |
| Devices → Pending hosts | device:approve |
| Devices → Update attributes & Delete | device:manage |
| Devices → Show configuration | configuration:read |
| Device → Connect to console | remote-access:connect |
| Configure | configuration:read device:read |
| Configure → Modify | configuration:manage |
| Configure → File selector | files:read |
| Configure → User & Ports Popups | inventory:read |
| Files manager | files:read |
| Files manager → Write access | files:manage |
| Logs | reports:read |
| Logs → Mark as read | reports:acknowledge |
| Map | inventory:read |
| Audit | audit:read |
| Audit → Show reports | reports:read |
| CVE | cve:read |
| CVE → Manage | cve:manage |
| Remote console | device:read inventory:read remote-access:connect |
| Remote console → Manage | remote-access:manage |
| Analysis | analysis:read device:read |
| Bootstrap Keys | bootstrap-keys:read device:read |
| Bootstrap Keys → Manage | bootstrap-keys:manage |
| Company | company:read |
| Company → Manage | company:manage |
| Users | users:read |
| Users → Manage | roles:read users:manage |
| Roles | roles:read |
| Roles → Manage | roles:manage |
| Order subscription | billing:read |
| Order subscription → Manage | billing:manage |