Develop and deploy devices like never before
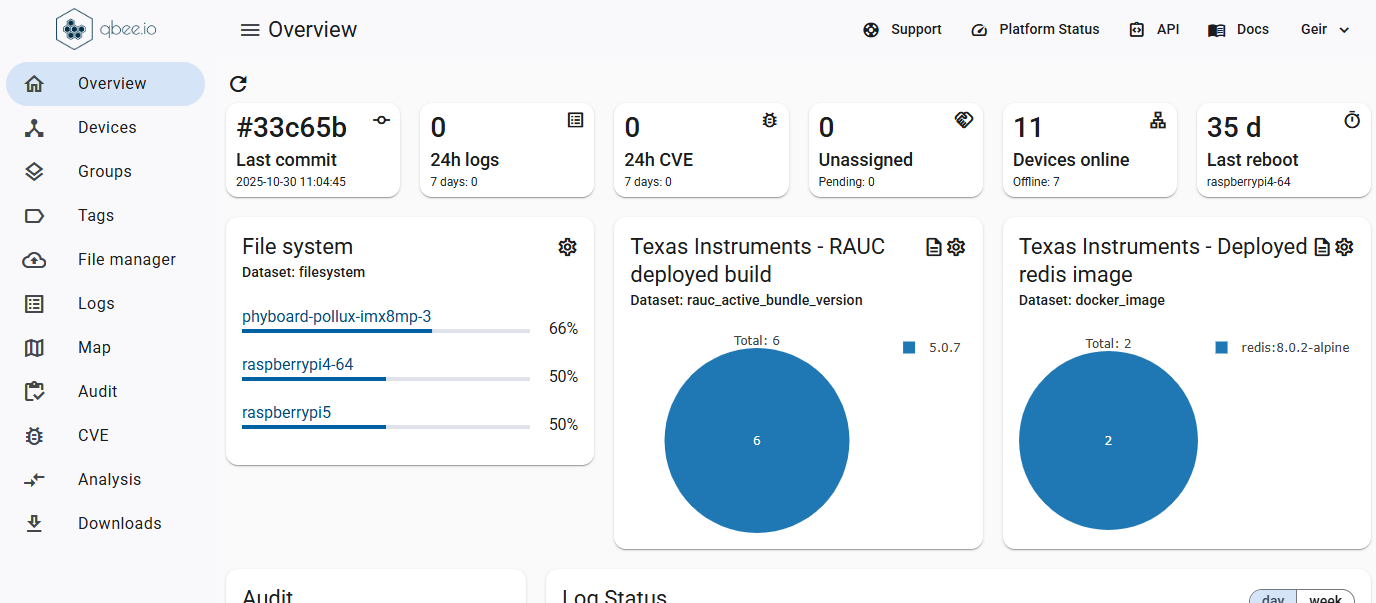
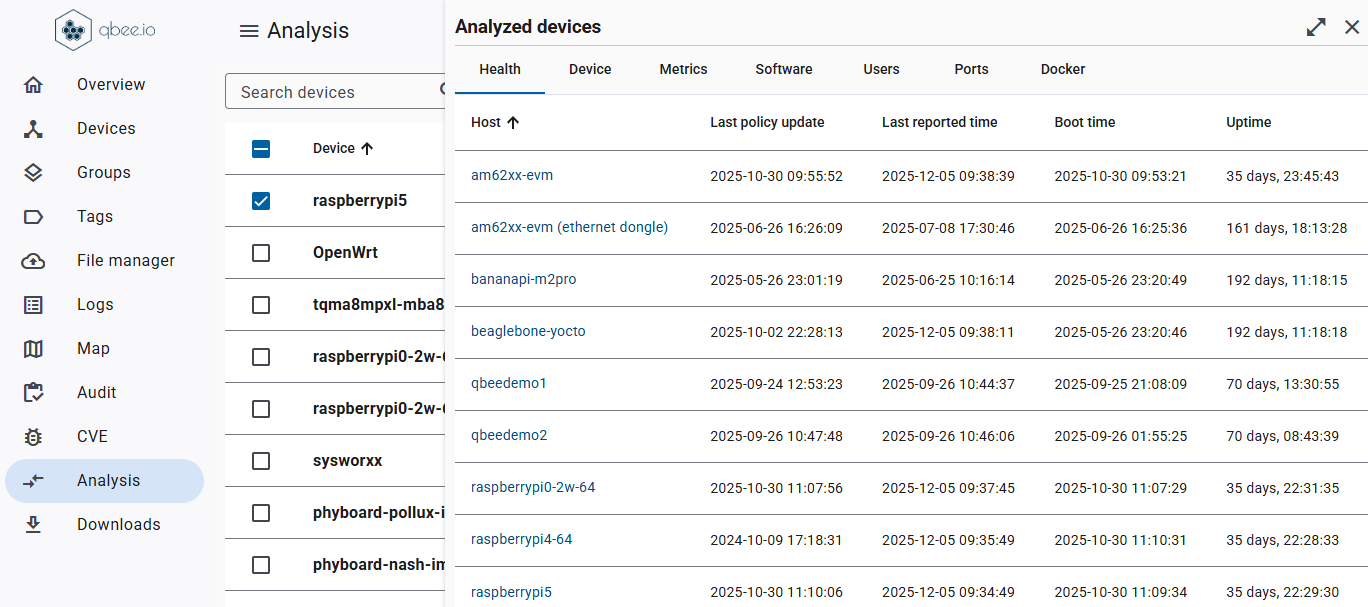
The seamless integration of the the embedded Linux OS, development and deployment process, device monitoring, and remote access allows you to focus and accelerate your Product Development.
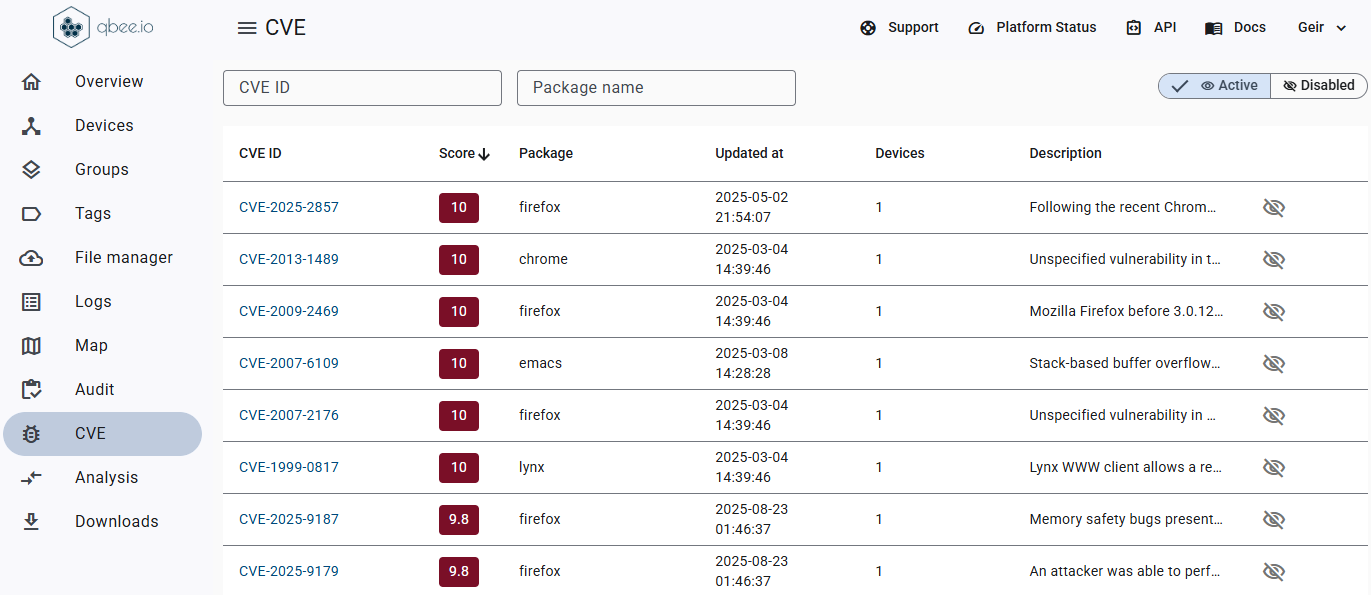
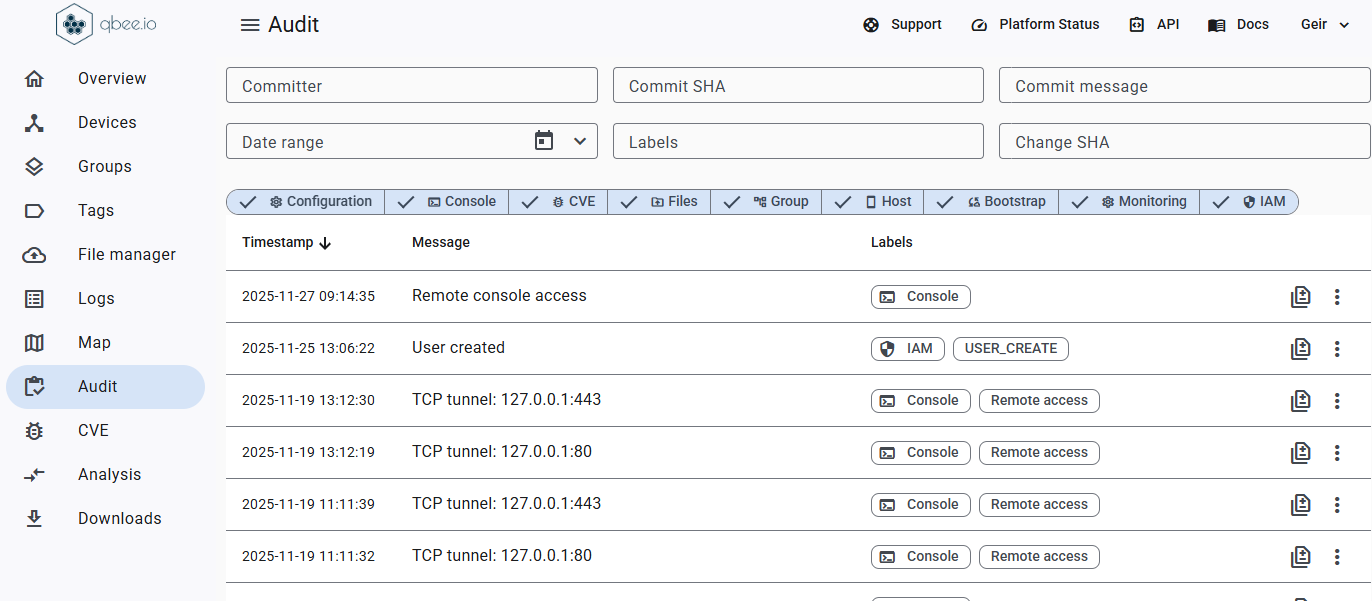
Stop wasting time on device management. Qbee automates updates, security and remote access, so your team can focus on building great products.
.svg)
.svg)

.svg)
.svg)
.avif)