Learn about the sudo vulnerability CVE-2021-3156 and experience how you can patch large numbers of devices within 5 minutes to protect your IoT or server infrastructure from this critical exploit.
In most Linux and BSD systems there is a 10 year old root privilege escalation vulnerability. This is labelled CVE-2021-3156 in the NIST database. Local attackers without root privileges can escalate their user to root privileges through a sudo command. In essence a simple backslash in the “sudoedit -s” command causes a heap based buffer overflow. This allows to execute an attack that escalates root privileges for any user.
In order to manually test your system if this vulnerability applies please run the following command sudoedit -s /. If a "sudoedit:" is displayed in the output the system is vulnerable. A "usage:..." shows that it is not vulnerable. This problem has existed since July 2011 and applies to old sudo versions like 1.8.2 to 1.8.31p2 as well as to current versions 1.9.0 until 1.9.5p1.
Since sudo is a very basic package this vulnerability exists on most Linux and BSD systems and action needs to be taken urgently. qbee.io helps you to analyse your infrastructure and discover which devices are exposed to this security risk.
If you look for the CVE or the command it impacts (“sudo”) you will immediately see how many devices are impacted.
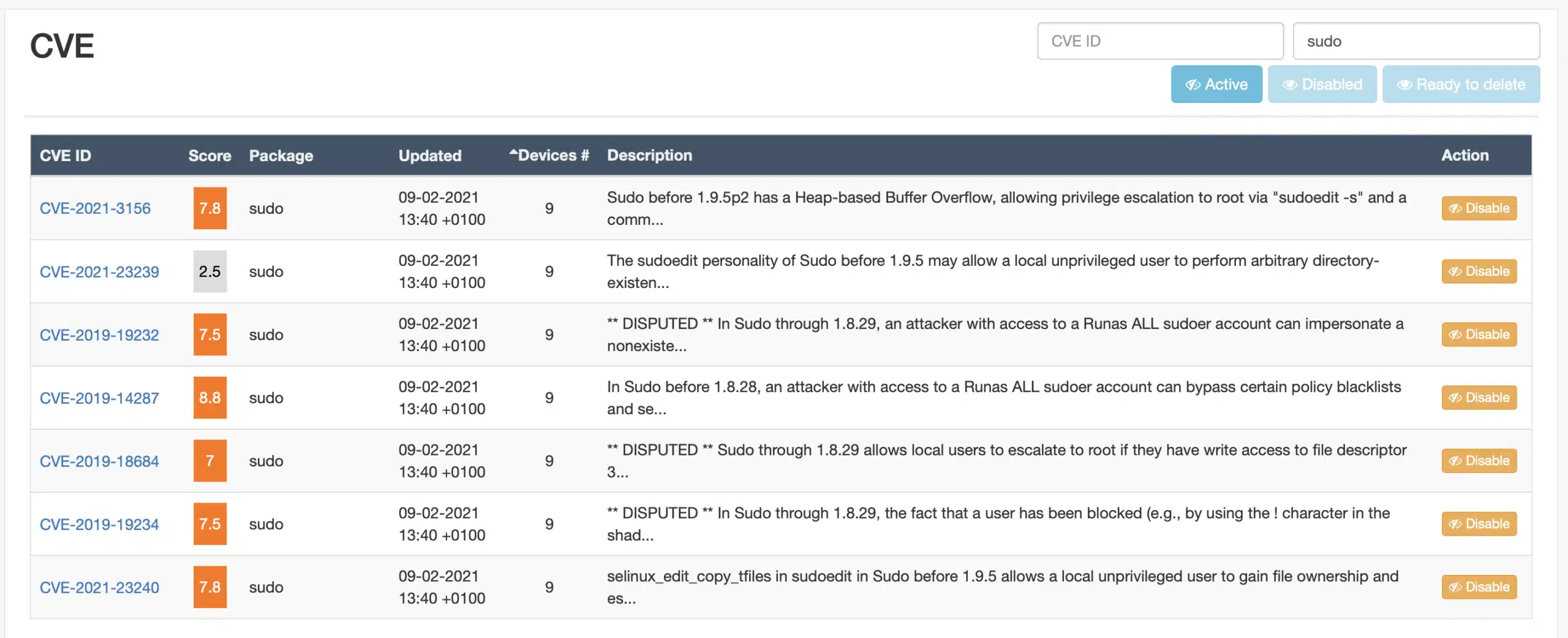
Clicking on the top CVE brings you to the specific page for this:
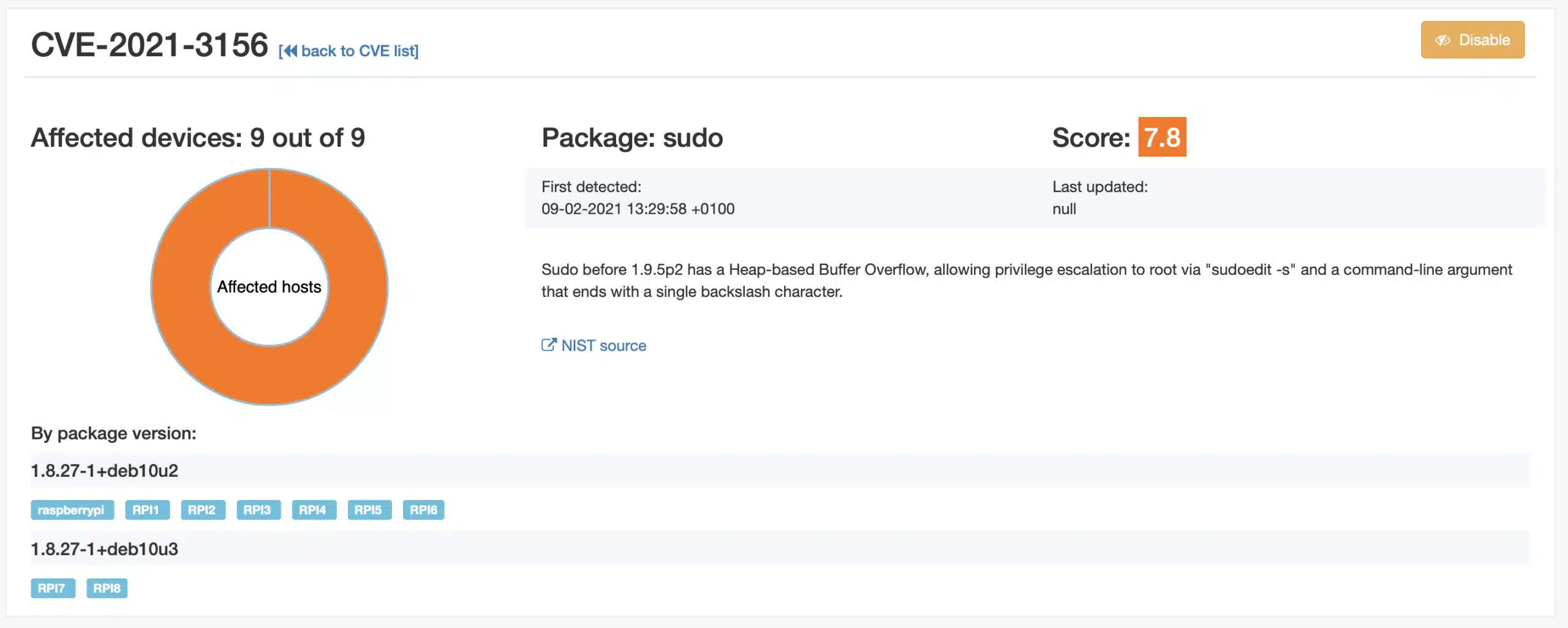
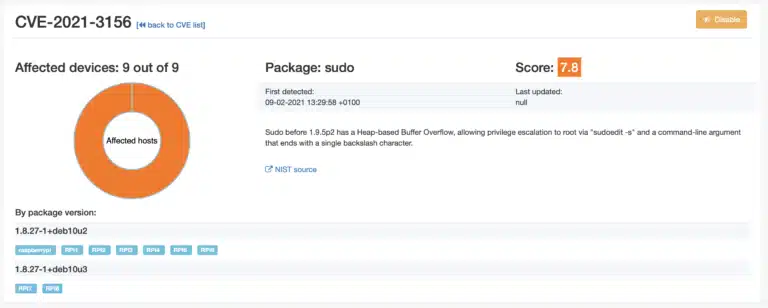
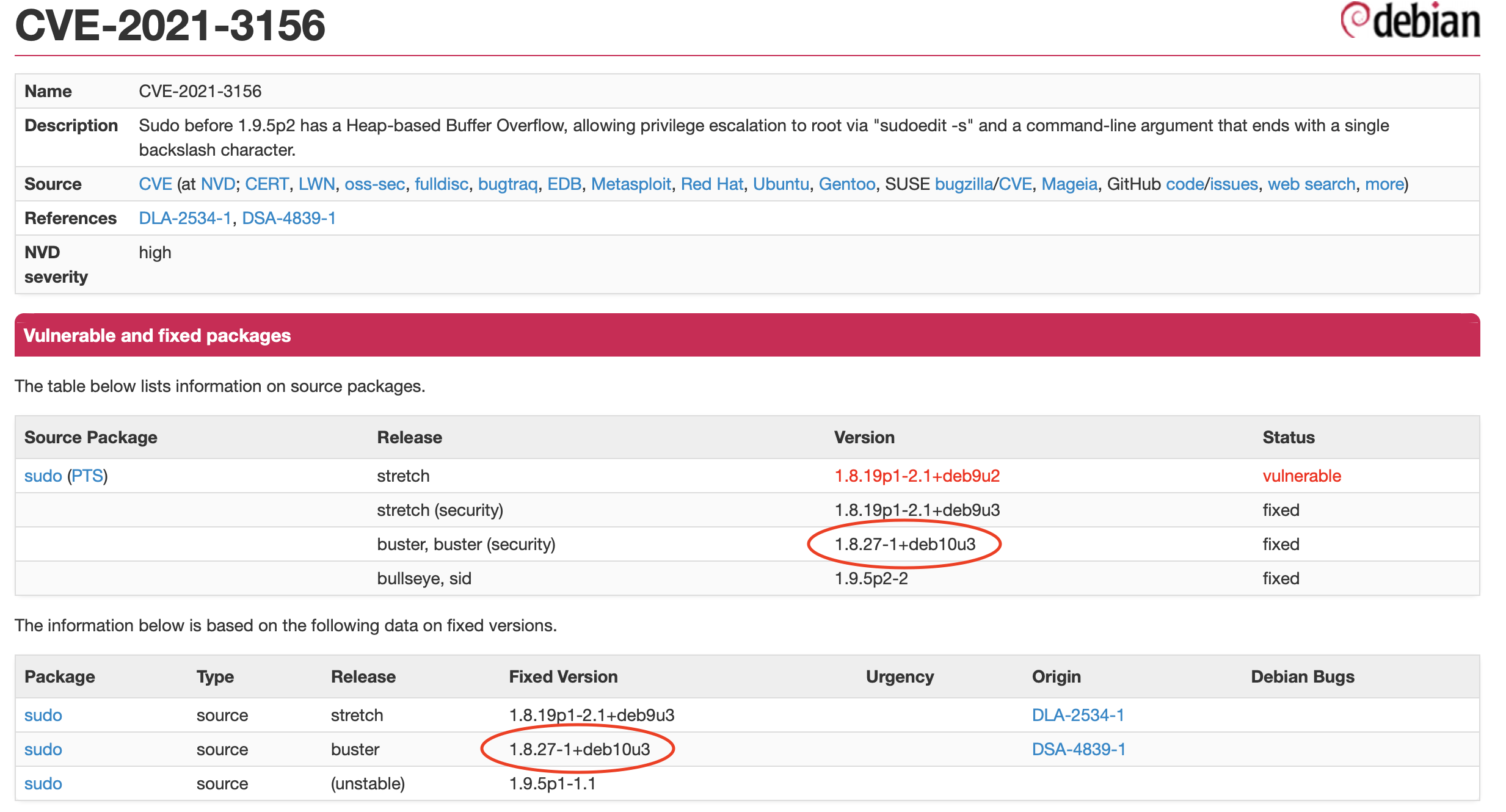
It can be seen that 7 devices have sudo package version 1.8.27-1+deb10u2 and two have 1.8.27-1+deb10u3. These last two devices are on auto-update and the Raspbian distribution has released a Debian fix for the Raspberry Pi. This can be checked on the respective security page for Debian packages.
From here you can simply use qbee to update to this specific version by using the OTA update and package management function. Please note that we used device RPI7 and RPI8 as test devices. Here we already have done the update and checked that the system is OK and stable. Now we move this into production for all devices.
There are two ways to do this. Either sudo is specified without a version and it will always update to the latest or we define a specific version. The later is done here and gives more control while the first ensures that sudo will always be moved to the last version. Please also note that the pre-condition can be used to do this at night, on a Sunday or when a machine is not running (by querying controller inputs with a script).
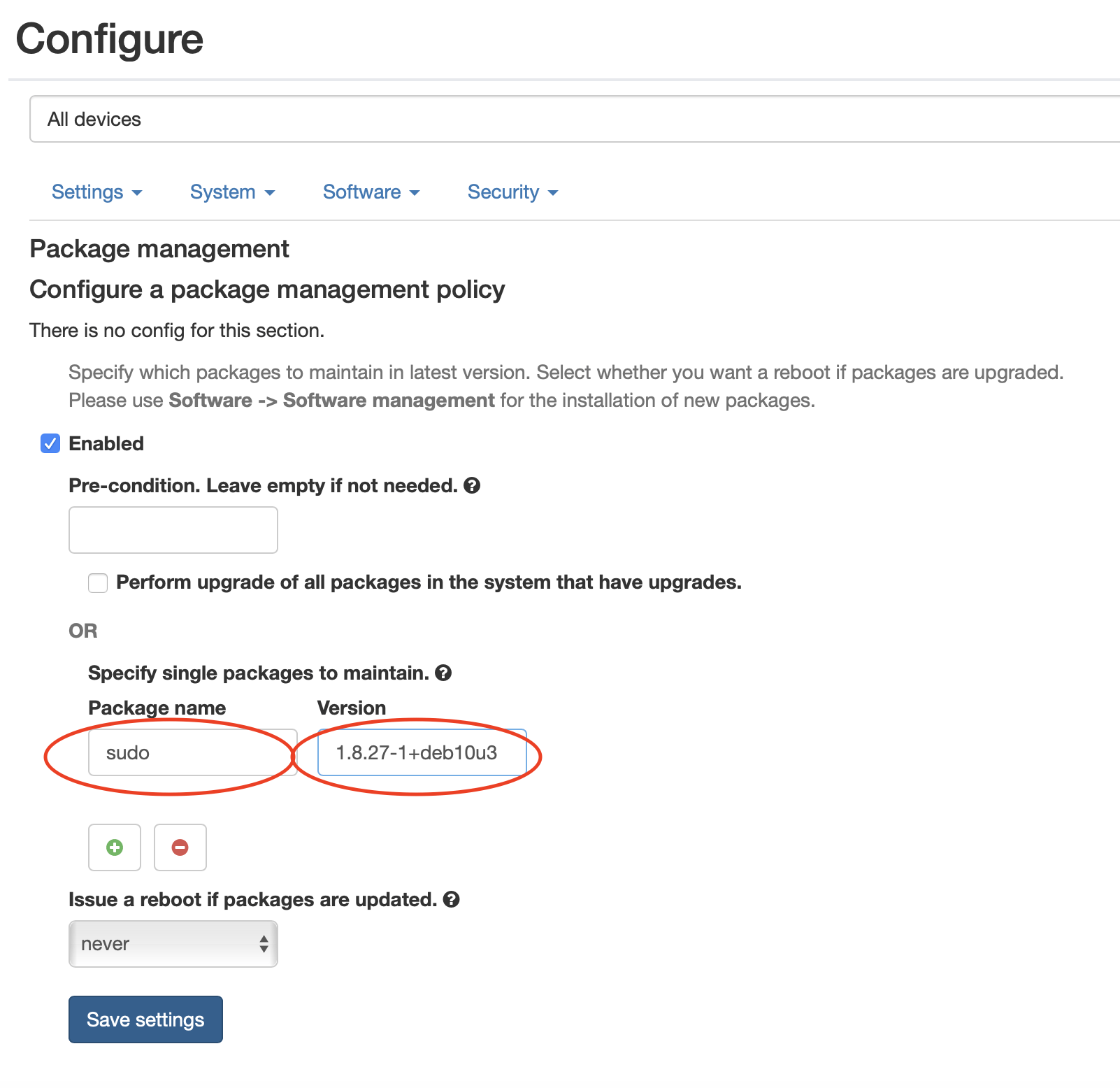
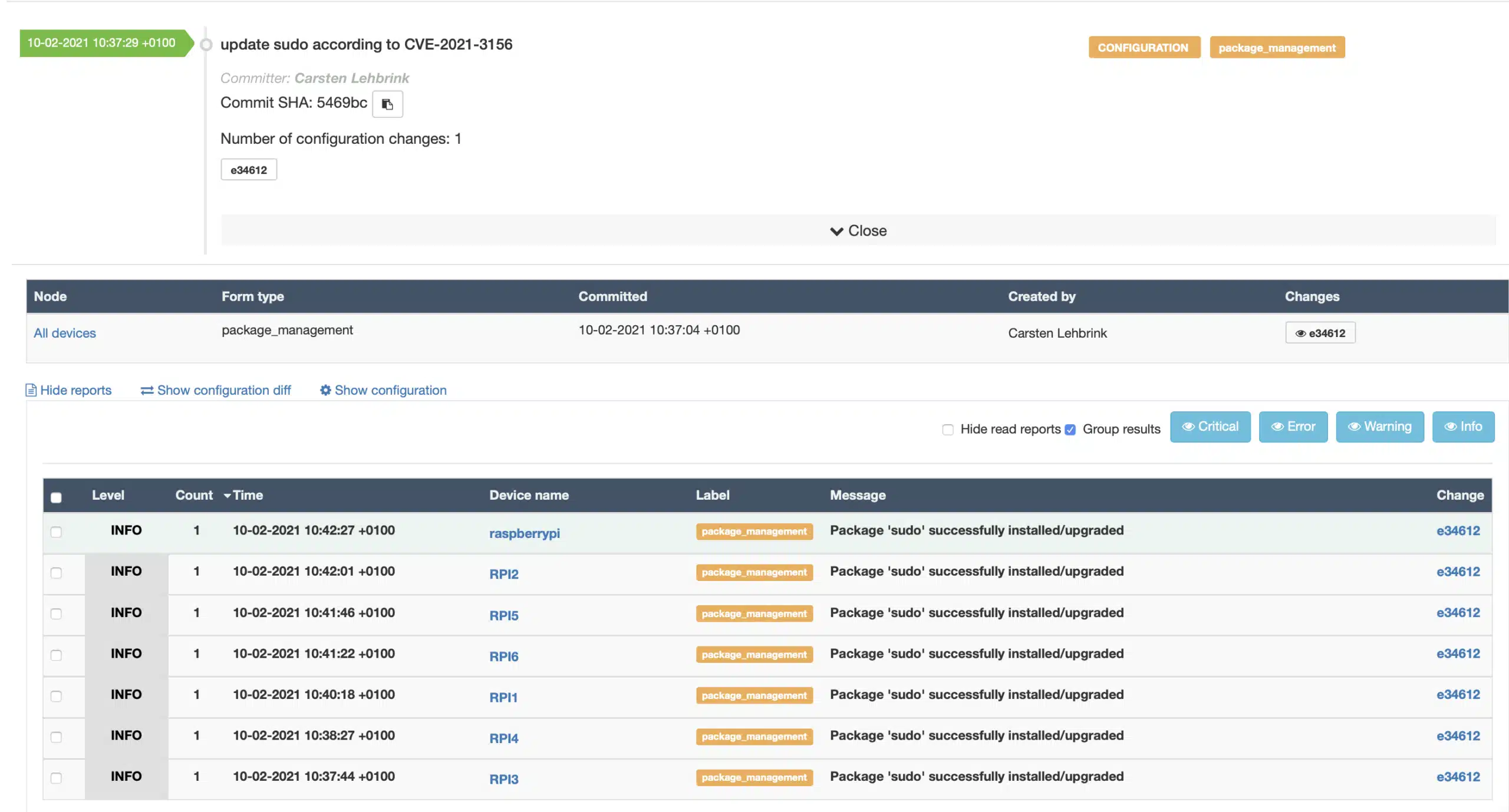
This new configuration is saved and committed and then we can see this in the qbee audit trail. All expected devices have successfully installed the update after one agent run interval (typically 5 minutes). Please note that you can patch thousands of devices within 5 minutes as each agent on the device will do this autonomously. Working as a autonomous pull based system also new devices that are moved into the group “All devices” will automatically updated:
Going back to the CVE view it can be seen that all devices are now on version 1.8.27-1+deb10u3 and thus are save. It can take a few minutes before all are processed again after the software update. Now you can disable the CVE or leave it in the system if you want to track this further.
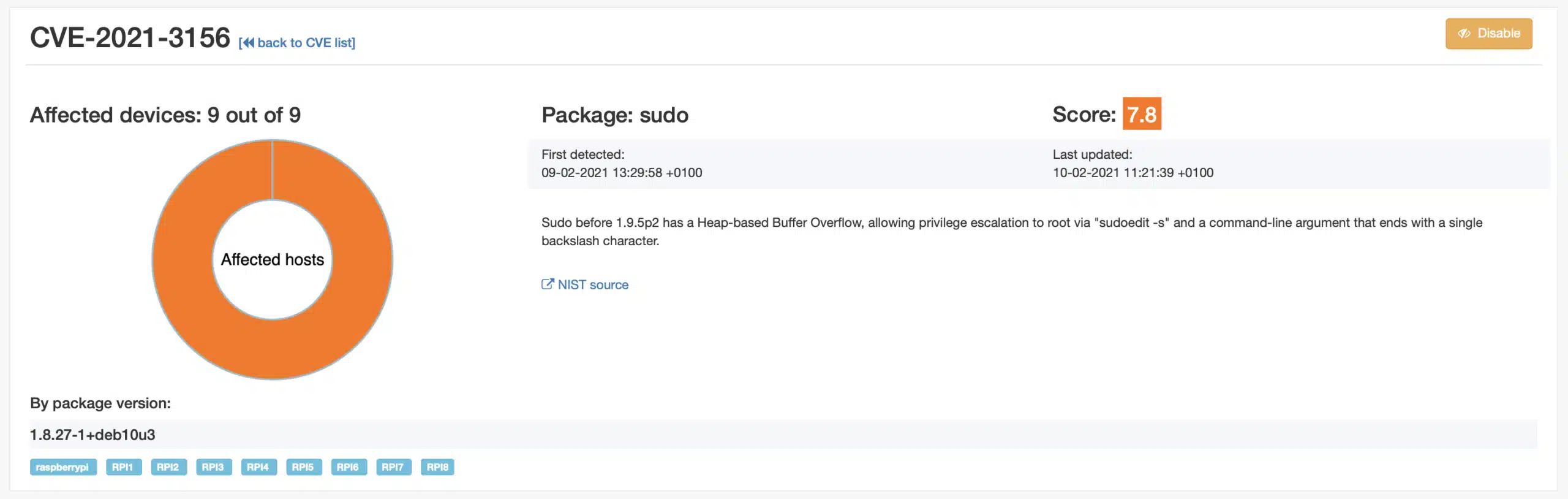
Eventually, when the repository moves to a version equal or higher than sudo 1.9.5p2 the CVEs will vanish and nit be counted anymore in qbee.io.
Please visit our trial page for a free 30 day qbee.io trial.