Today we want to present a demo called “IT security – know your neighbours” with the subtitle “…applied ssh port forwarding”.
It demonstrates an old functionality called ssh port forwarding that even IT experts consider very rarely. But this can have a huge impact on your network security. Below you see the video and then we have a transcript with some additional information.
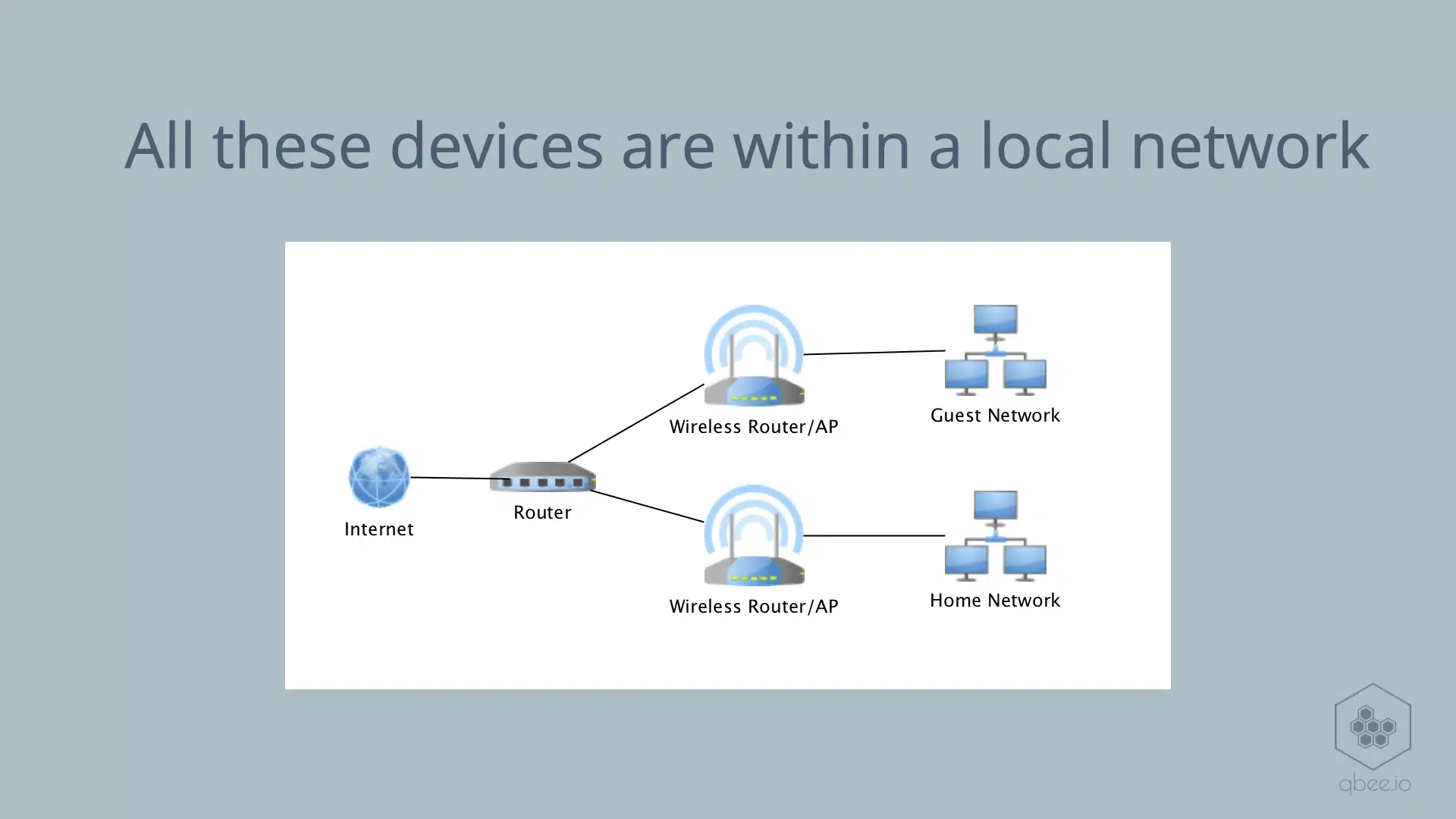
Today we have many devices in our company or home networks. This is especially true since IoT or the Internet of Things started to grow. It is important to understand what type of devices we have there and what they are capable of in order to maintain IT security.
All devices within one network can theoretically see each other and contact each other.
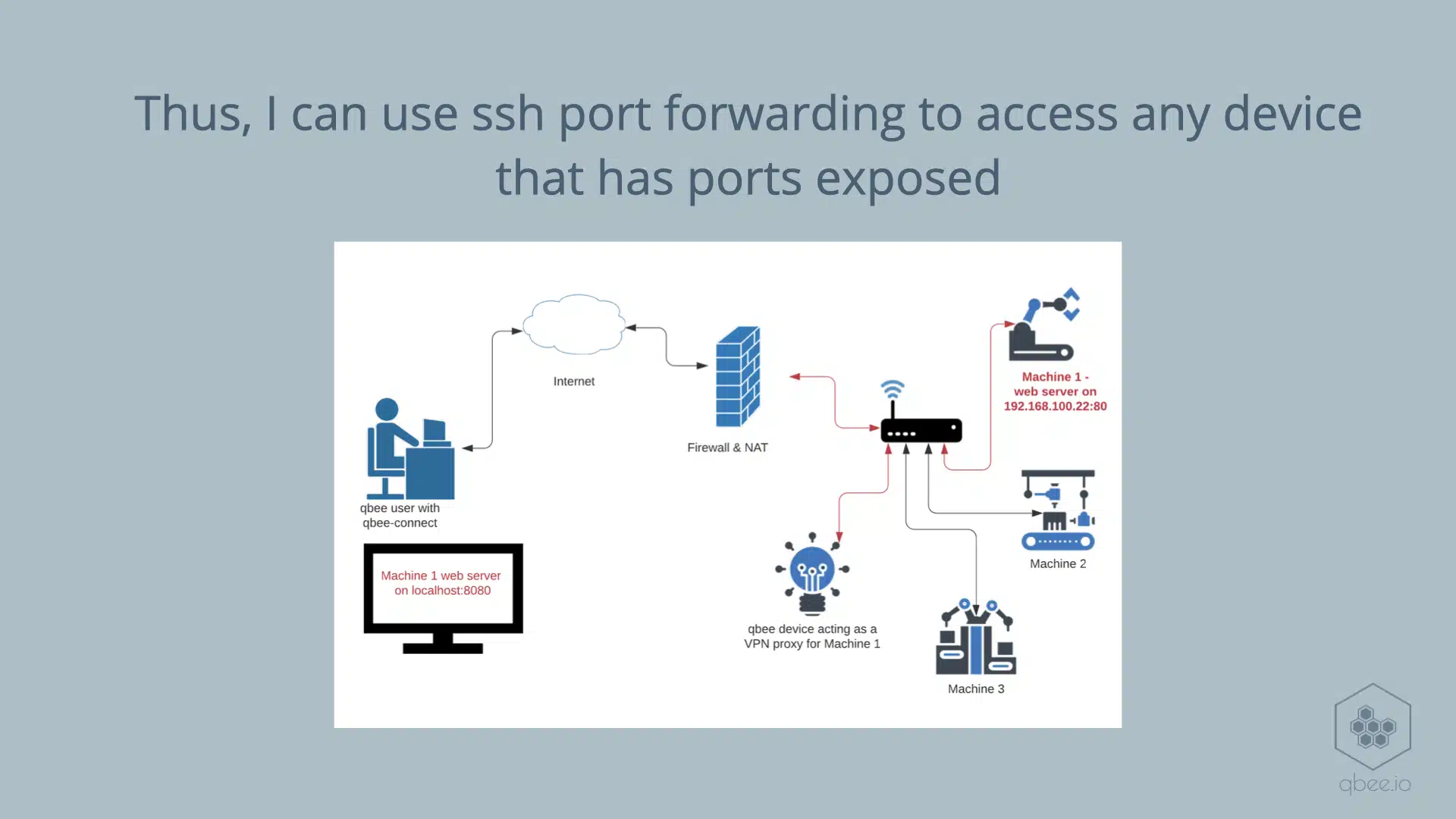
This allows a device to use a technique called ssh port forwarding to access other devices’ ports as long as they are open.
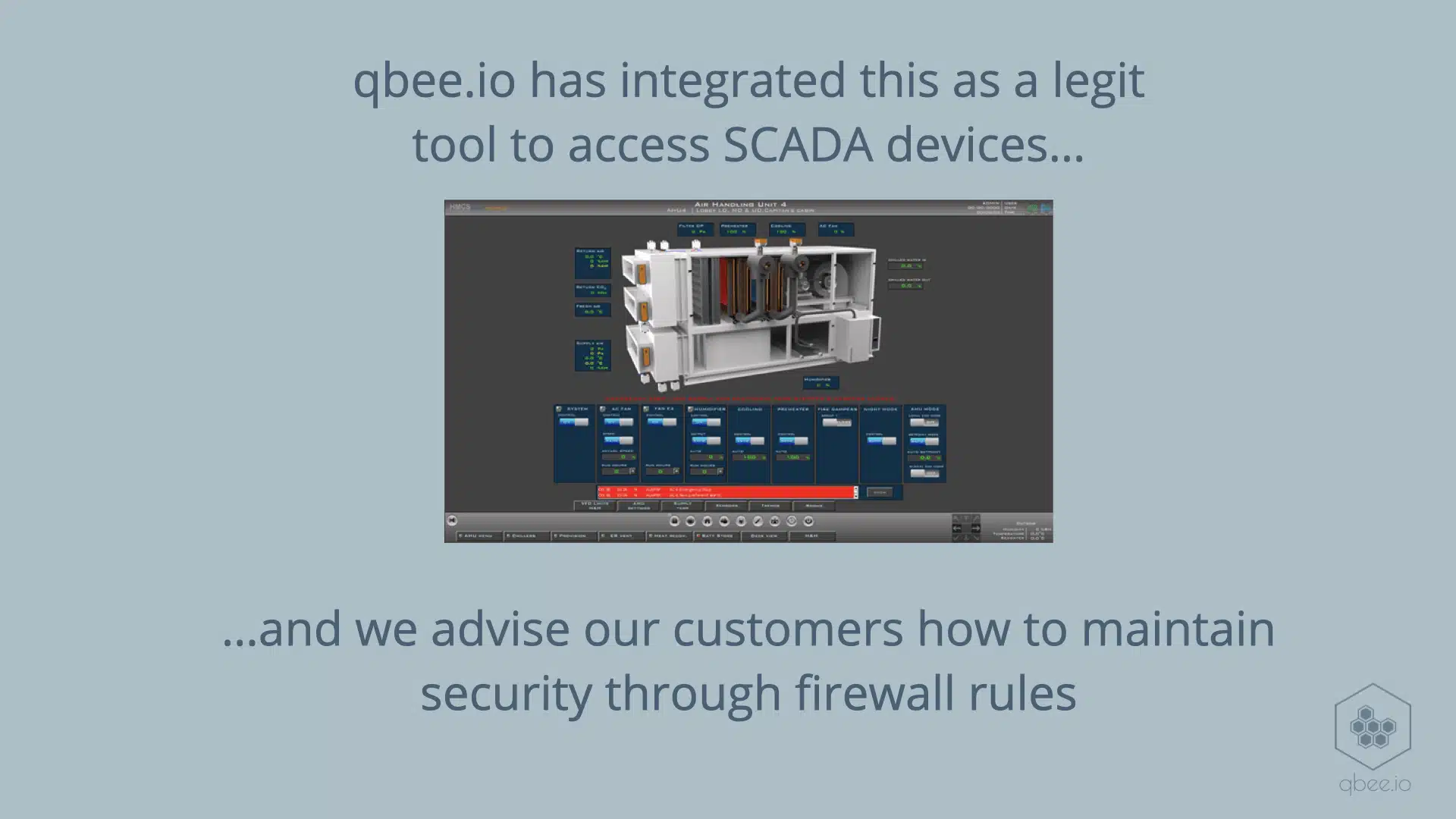
Qbee.io has this functionality built-in and this is used to access legacy SCADA applications. We advise our customers to configure a firewall on the other device to only allow the qbee device to access that specific port.
Because in theory any device that has a network interface and a TCP/IP stack can access any other open port in a local network. Even if we are talking about a tiny smart lightbulb.

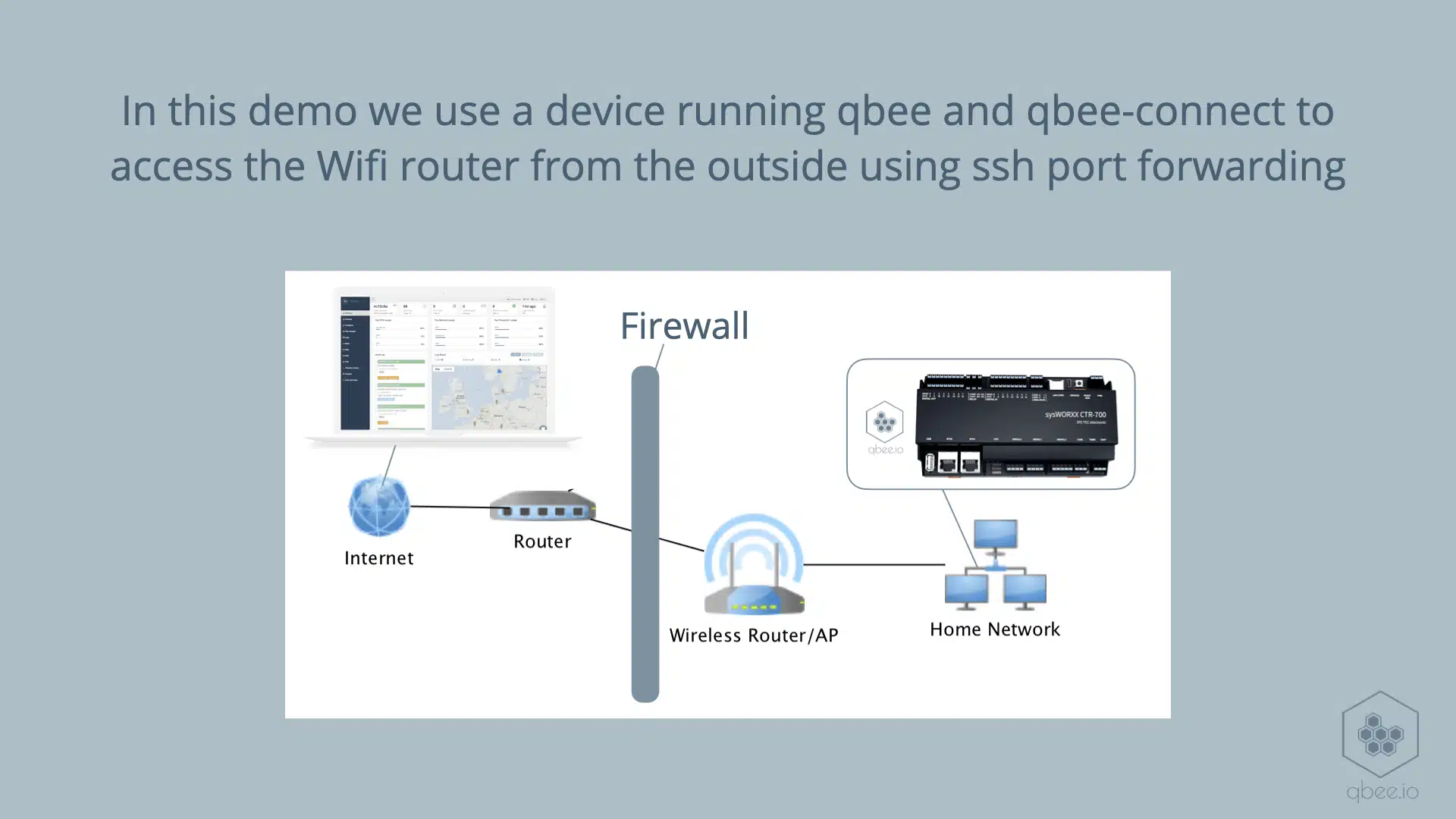
In this demo we have a qbee enabled controller in the remote network. The network is completely blocked by a firewall for incoming connections. Still, we use the desktop tool qbee-connect to do a ssh port forwarding from the qbee device to the wireless router. This wireless router is a standard consumer device. In this case we use a D-LINK but any router usually exposes port 80 or 443 for configuration purposes.
In this demo we have a qbee enabled controller in the remote network. The network is completely blocked by a firewall for incoming connections. Still, we use the desktop tool qbee-connect to do a ssh port forwarding from the qbee device to the wireless router. This wireless router is a standard consumer device. In this case we use a D-LINK but any router usually exposes port 80 or 443 for configuration purposes.
Let’s start with the real demo then (again, video available above).
The device in the remote network is running the qbee device management software. We use the qbee-connect desktop tool and the built-in VPN to establish an ssh connection to the device from anywhere in the world.
Then we open the advanced settings of the tool and define the target remote IP address of the router, the port we want to address it on, and the local port to which we want to map the router UI application. In this case this is port 8080. Then we connect this. Now we have mapped the remote router port 80 through the qbee device and a secure firewall to localhost port 8080.
Now we can access it using our local browser.
As with most routers the D-Link DIR655 has a standard user and password (password is actually empty…). If this was not changed even the smart lightbulb could now re-configure your router by opening additional ports or this could be used for an attack on your NAS or file server.