The internet of things (IoT) is nothing new. It has been around for decades, previously often referred to as M2M (machine to machine) technology.
In this article we want to focus on four key megatrends that need to be investigated closely to understand why the pressure for security and regulation in IoT is increasing. In this first part we investigate these key trends. In the second part we will expand on current and future regulation initiatives and comment on the key drivers behind those.
1. IoT megatrend – exponential growth of the number of devices
The number of IoT devices is growing rapidly. It was estimated that in 2020, around 30 billion IoT devices will be in use. The expected growth will accelerate sharply in the future up to more than 100 billion devices.
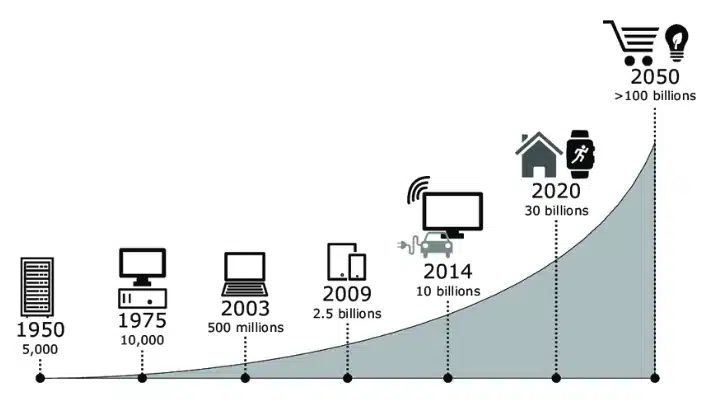
The more devices that are deployed in the field the higher the number of devices that are potentially vulnerable. This increases the number of devices that can be harmed or that can be hijacked to do harm to other infrastructure. Examples of the latter are botnet attacks, such as DDOS (distributed denial of service), against other infrastructure [1].
Potential problems that come with the increase in the number of devices, can also be reinforced by megatrend 3. Re-using software components, operating systems or libraries causes larger pools of devices to be vulnerable. Thus, one specific component can cause an extremely large number of devices to become vulnerable by the same attack. These devices can sometimes even be conveniently discovered by specific search engines such as https://www.shodan.io.
Here is a simple example to illustrate the point (these numbers are just examples and not researched): Assuming that 1% of the above-mentioned 20 billion devices are embedded Linux devices. This gives us 200 million embedded Linux devices. If we also assume that only 1% have an unpatched Heartbleed OpenSSL vulnerability, we are still left with 2,000,000 units that can be attacked.
F-Secure has detected 5.6 billion attack events in 2019 with IoT being the dominant attack targets. This includes brute forcing usernames and passwords but also typical protocols [2].
This graph shows the registered TCP port attacks just for 1H 2019:
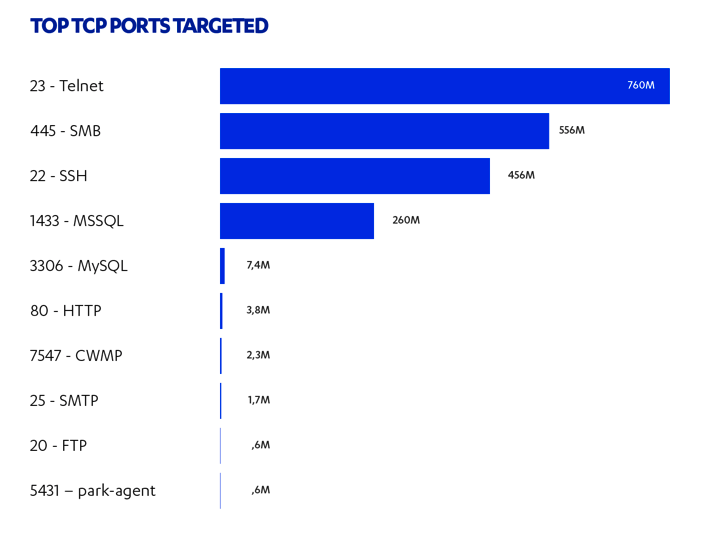
Source: https://blog.f-secure.com/attack-landscape-h1-2019-iot-smb-traffic-abound/
2. IoT megatrend – the air gap is being removed
Previously many M2M or IoT devices were deployed in scenarios where no direct connection to the internet was possible. This is also known as an “air gap”. But the continuing digital transformation of industry and society, along with an increased demand for interoperability and data exchange, has removed many of these air gaps. Previously, it was considered bad network architecture to connect an industry shop floor. Today this is common everywhere because companies want to benefit from predictive maintenance, advanced resource planning and much more.

In essence, critical parts of industrial infrastructure, the power grid and the communication infrastructure are fully or partly connected to the internet. Usually there are protective systems in place, but no security mechanism is perfect. Devices might experience operating conditions in which they are accessible from the outside or by another internal device that has outside connections. This problem is even more present in consumer IoT. Smart electricity outlets, smart TVs, security cameras and smart home systems open many connections into and out of our homes. Any of these devices can be used to attack other devices in the local network in order to steal sensitive data or cause havoc. With standard consumer Wifi routers and network switches this is very difficult to detect or to fight.
The next big advancement in the development of the electricity grid is dynamic load switching. This aims to stabilize and balance the power grids and is a very powerful technology that can save additional CO2 pollution by reducing the needed power overhead and balancing energy consumption locally. If we assume a home with an electrical vehicle charger, an electrical warm water boiler and electrical heating/cooling system, this will yield a large power reserve that can be switched when brought online. In regular operation this is used to balance peaks or overproduction of electricity. But if one provider is using a homogenous system that is attacked either directly or indirectly through other common devices, large local load jumps can be created. This attack can effectively destabilize the power grid or even cause a blackout. All this has to be considered when removing the “air gap” and connecting and actively controlling electricity loads through the internet. This potential danger should be reflected in regulation as well.
3. IoT megatrend – shared systems, libraries and operating systems
Legacy M2M systems often used proprietary means of communication and due to cost concerns were built on non-standard OS systems or without any OS at all. Today, from a cost perspective, it is feasible to use different standard operating systems on all devices that demand a certain application complexity. This actually decreases the development costs. Also, these applications usually deploy a lot of shared libraries. This helps developers to create much more powerful applications faster, but it makes the device base much more homogeneous. If a security problem is discovered it will impact many devices at once. In addition, systems become increasingly more complex. This extends capabilities but also makes it more difficult to fully comprehend and secure the full technology stack. Typical examples are again the Heartbleed OpenSSL vulnerability but also the Tuya problem. Here one IoT manufacturer licenses a system to many different brands, but it is possible to attack the devices and exchange the firmware easily.
All these problems can only be prevented if the systems can be controlled and updated also after having been deployed and shipped. This raises the question who in the value chain needs to take responsibility for preventing and fixing any potential problems.
4. IoT megatrend – information density and sensitivity
Today most people and companies use a virus scanner and other protective measures on their personal or work-related computer. The reason for this is that most people would agree that they have a rather high density of information on the machine (thousands of mails, photos or documents) but this information also has a very high degree of sensitivity. Nobody wants others to have access to personal mail exchanges, images or business documents.
This problem has received a large amount of public attention as early as 1993 for the Michelangelo virus or in 2000 for the ILOVEYOU worm, just to mention a few. Therefore, both best practices and regulations are in place for servers and personal computers.
For M2M or IoT installations there was (and partly still is) a different perception. People would say things like: “How bad can it be if someone gets access to my electricity consumption data?”
“How bad can it be if someone gets access to my electricity consumption data?”
With some smart data analysis this allows someone to basically analyze the whole life of a family. This includes when people get up, go to sleep, if they watch TV or play on game consoles, how often they shower, turn on the dishwasher or washing machine, if they are on vacation and much more.
Most systems today are able to extract much more information than just temperature or electricity data and with machine learning and big data technologies this information reveals much more sensitive information implicitly.
This gets even worse if the security breach turns active. Devices can start to eavesdrop on network traffic or start controlling other devices (like the previously described attack on a badly secured smart power grid). This way the complete IoT infrastructure can be endangered and physical consequences can occur. It is possible to start multi-step attacks and change certain critical parameters basically unrecognized. This scenario is described in this very informative article how Stuxnet attacked the Iranian uranium centrifuges [3]. These examples show that M2M and IoT have become much more than just the transmission of a few temperature points or GPS coordinates. For many use-cases both the information density and sensitivity is so high that society cannot afford to neglect to protect this.
The trends described here raises questions of both technical (security) and regulatory nature. This deserves a more in depth discussion, so make sure to catch our next post where we will be expounding more on the current IoT regulatory environment and security measures.







